Validate Network Inspection
Let us validate inspection of traffic with the Network Security managed endpoint.
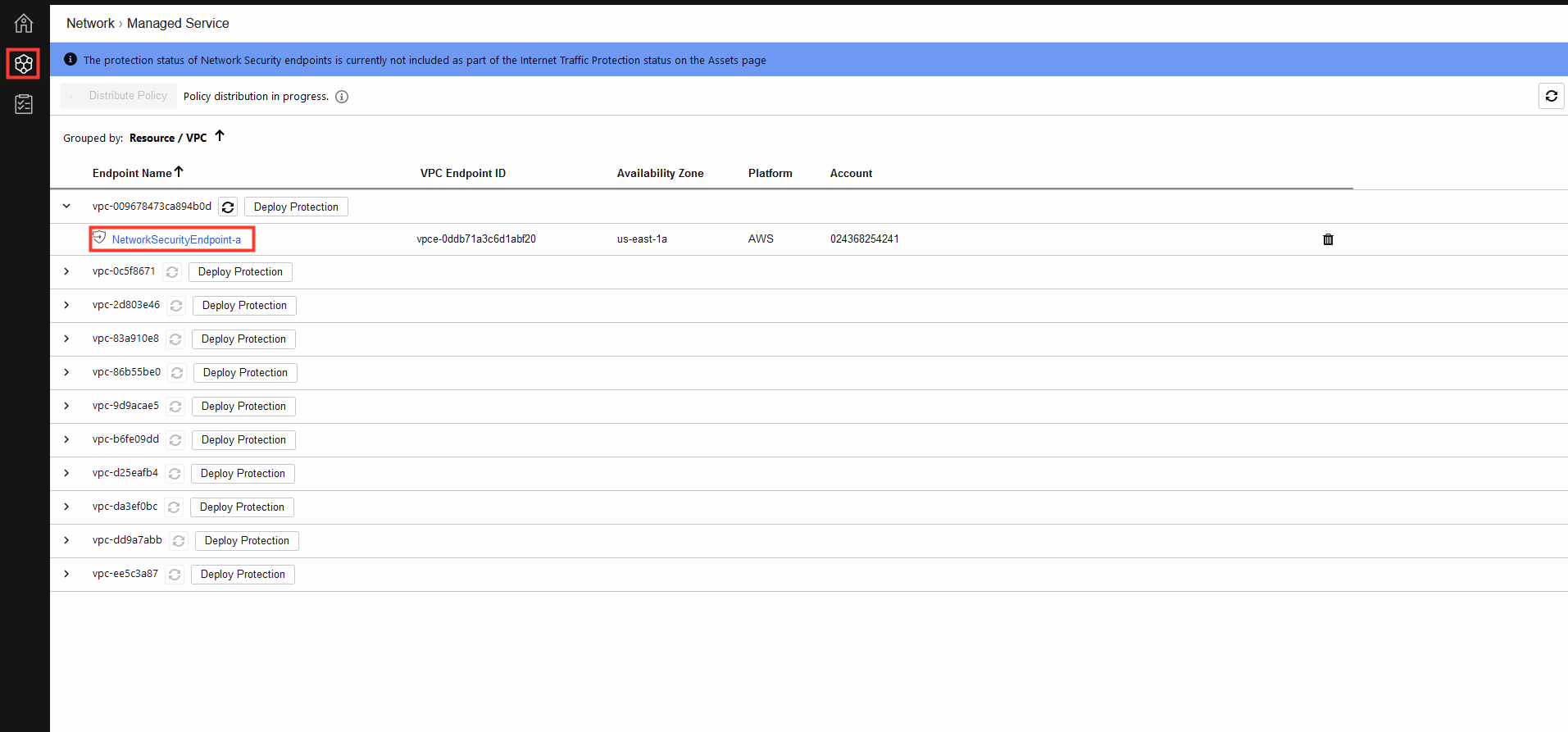
1. Distributing the Policy.
- In the Network Security Console select the Network tab.
- Click on Managed Service
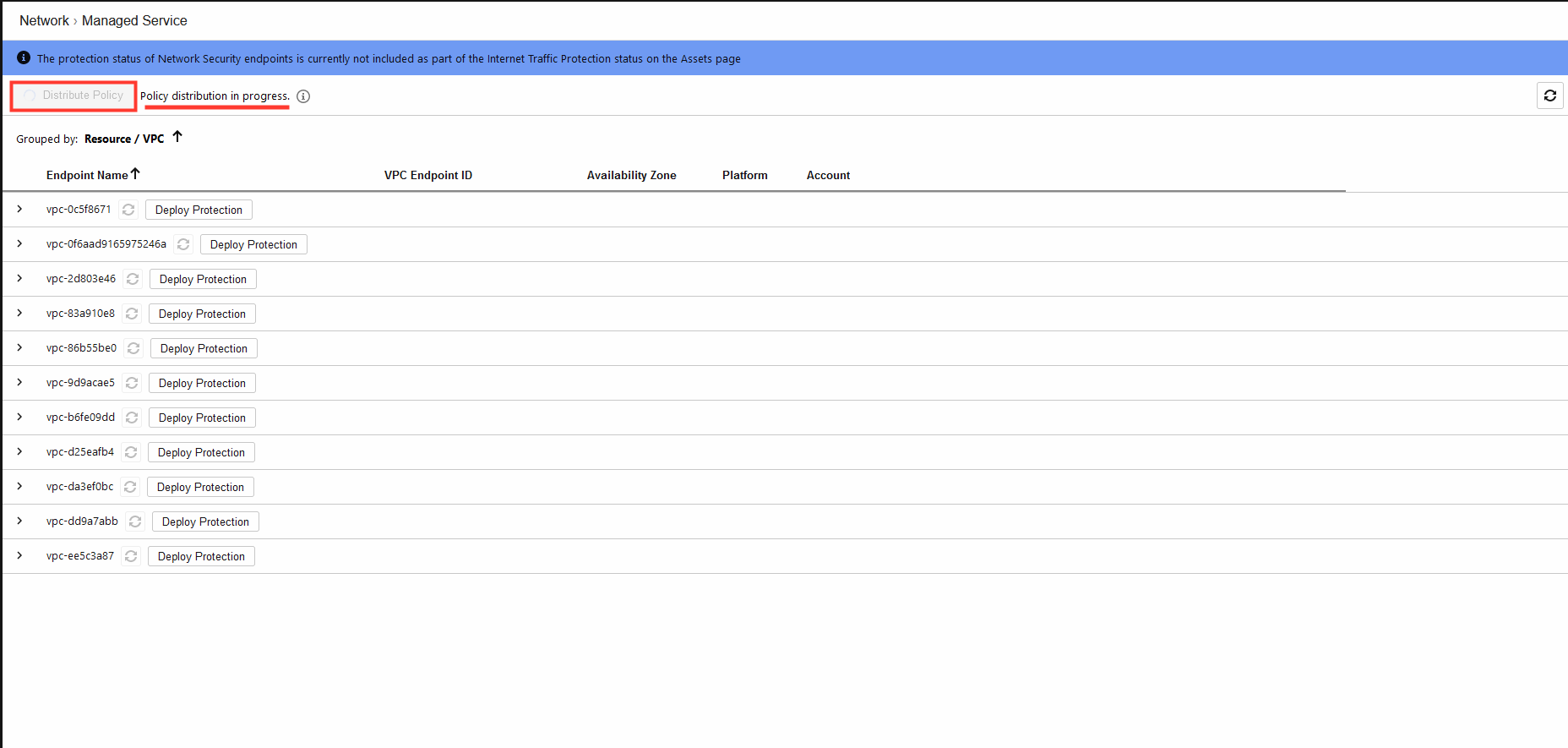
2. On the Managed Service page, click in Distribute Policy and wait until it distribution has finished.
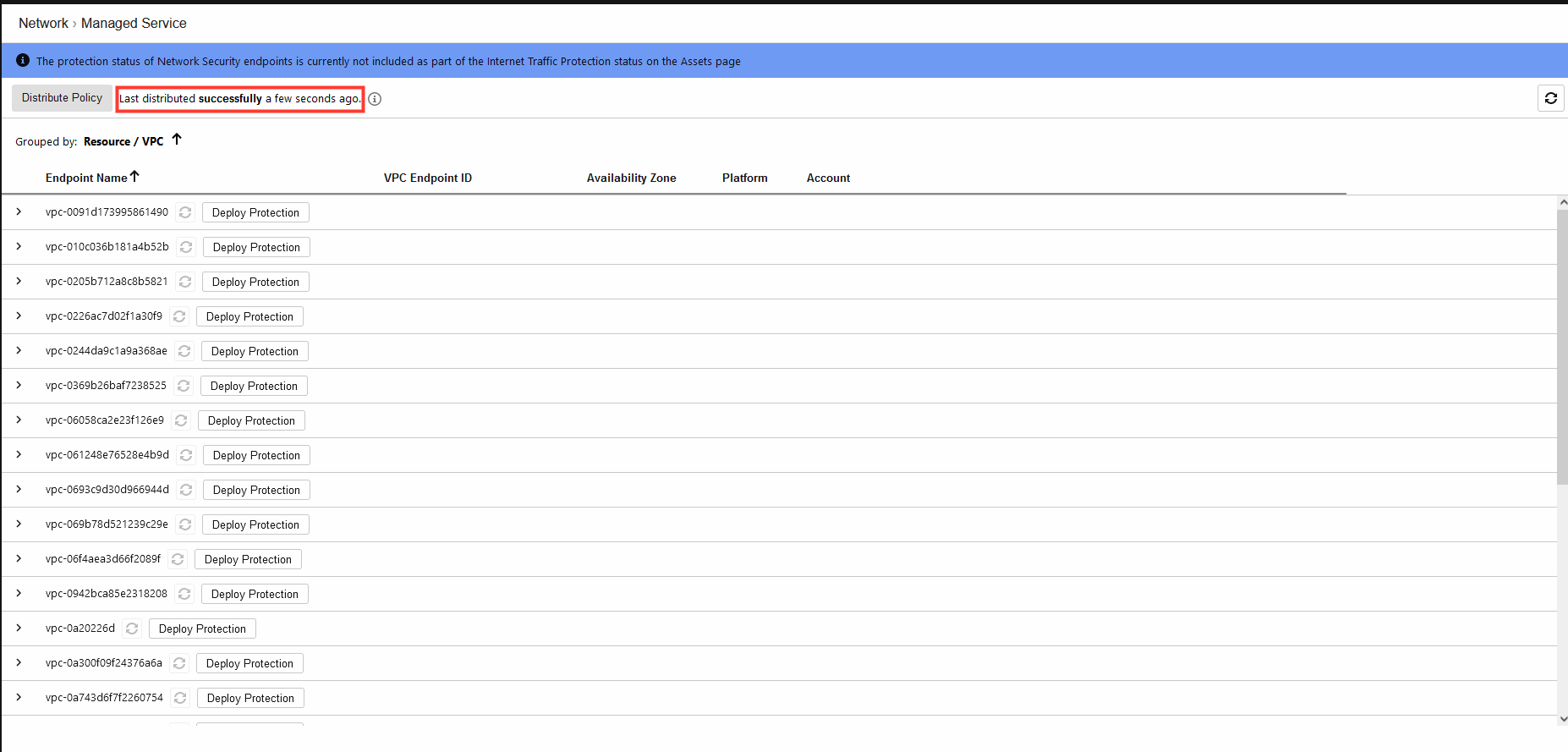
2.1 Once it finish it will look like the image below.
3. Validate deployment.
After you complete the deployment of the Network Security endpoints and modify your route tables, verify that deployment was successful from the Managed Service page.
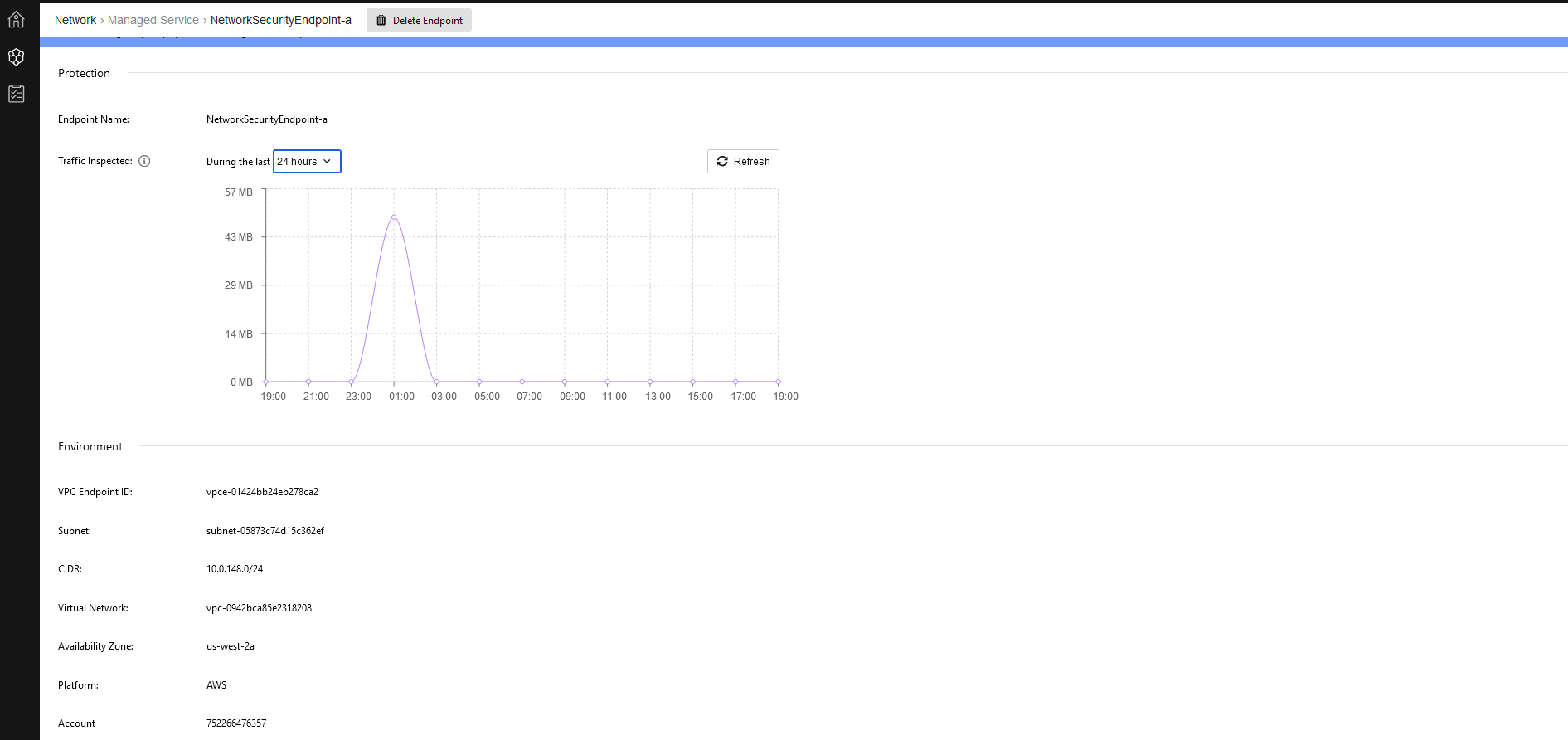
- Click on Network Security endpoint A link to view the protection details for that endpoint, including the rates and times of traffic inspected.
If data appears in the Traffic Inspected graph, then the managed service was successfully deployed. If not traffic inspection data appears, double check the routing in your cloud environment.
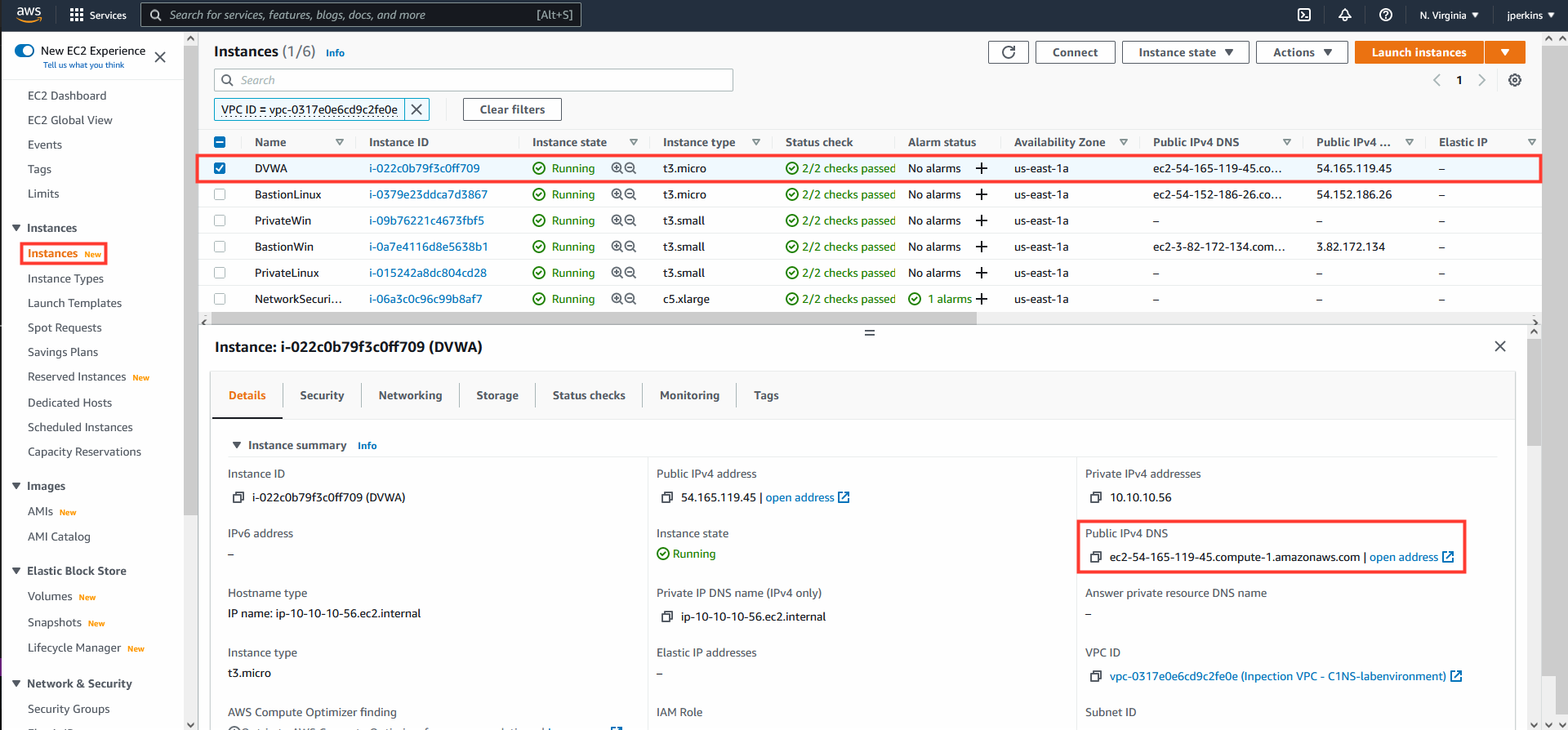
4. Navigate to the AWS Console
- Navigate to EC2
- Select EC2 instance DVWA
- Copy the Public IPv4 Address/DNS
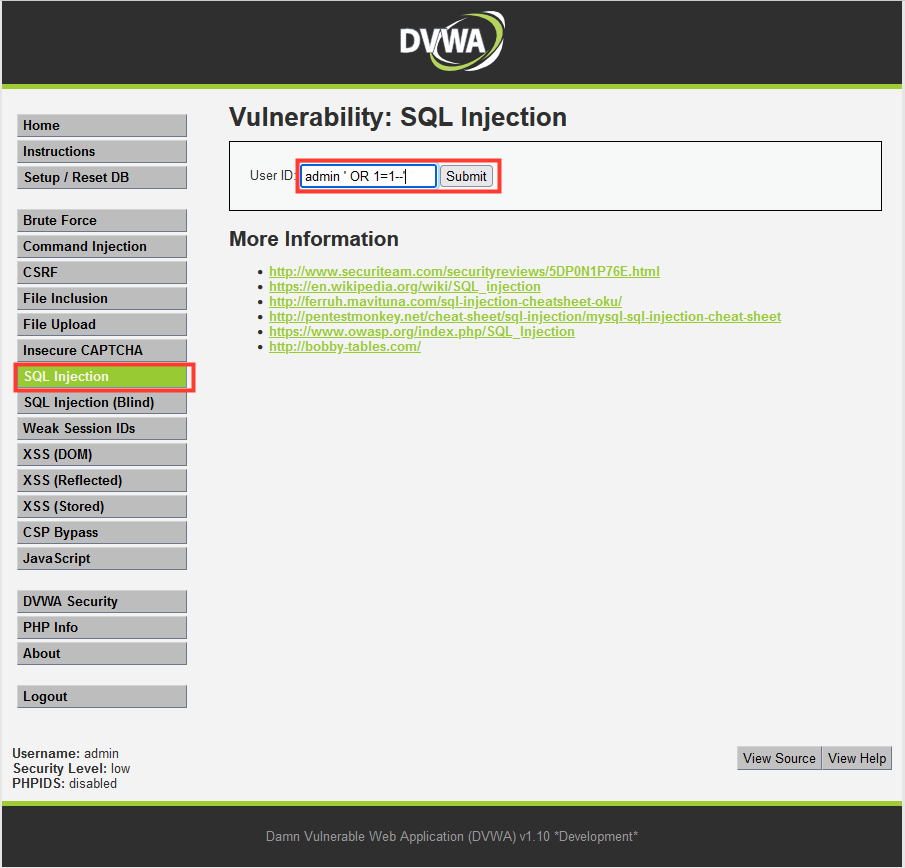
5. Access the web application using the Public IP/DNS.
- Remember that it will be over HTTP.
- User: admin
- Password: password
- Login

6. DVWA SQL Injection
-
Select: SQL Injection
-
User ID:
admin ' OR 1=1--'
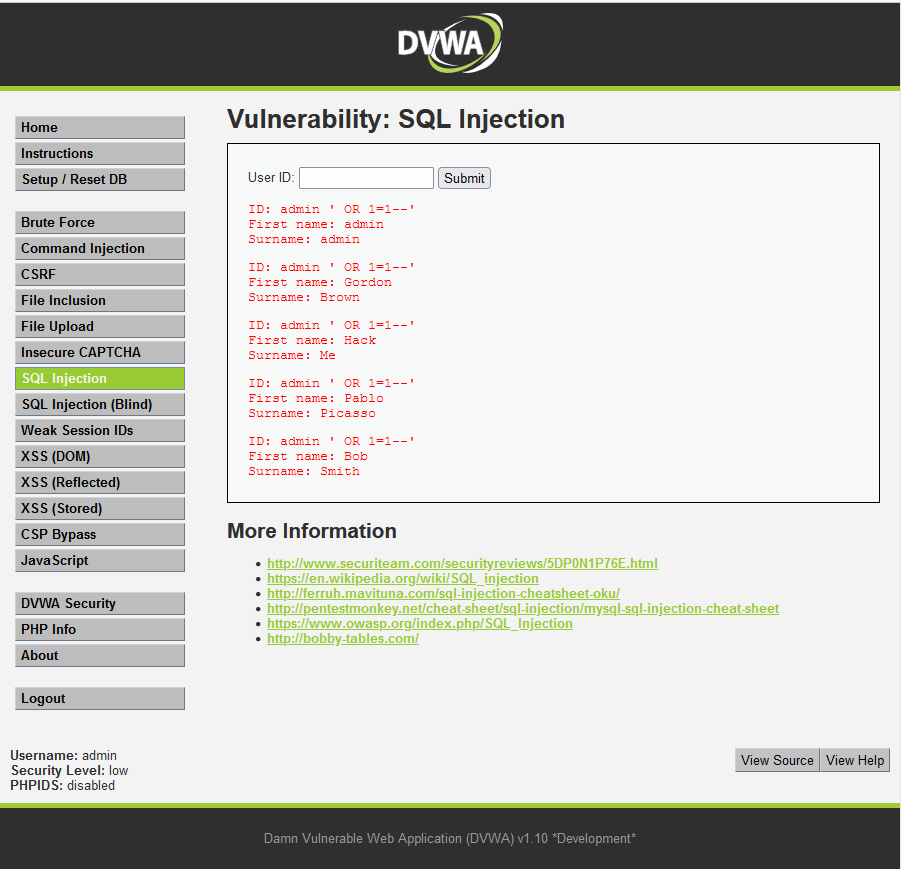
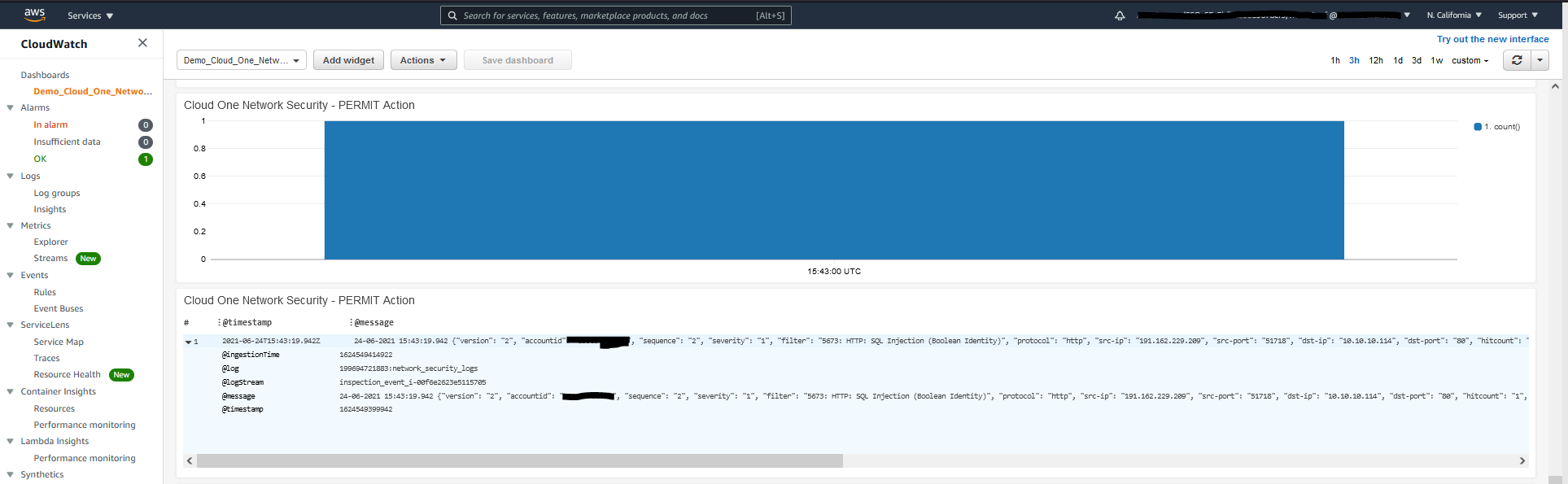
6.1 Remember we configured the SQL Injection filters to Permit, if you want to you can change it to Block. Let’s check our CloudWatch dashboard for the SQL event.
If you decide to change this intrusion prevention filter from permit to BLOCK you will need to redistribute the policy before it will take effect.
- In AWS Console navigate to CloudWatch
- From the left-hand menu select Dashboards
- Select: Cloud_One_Network_Security_Panel
- Check under Cloud One Network Security - PERMIT Action
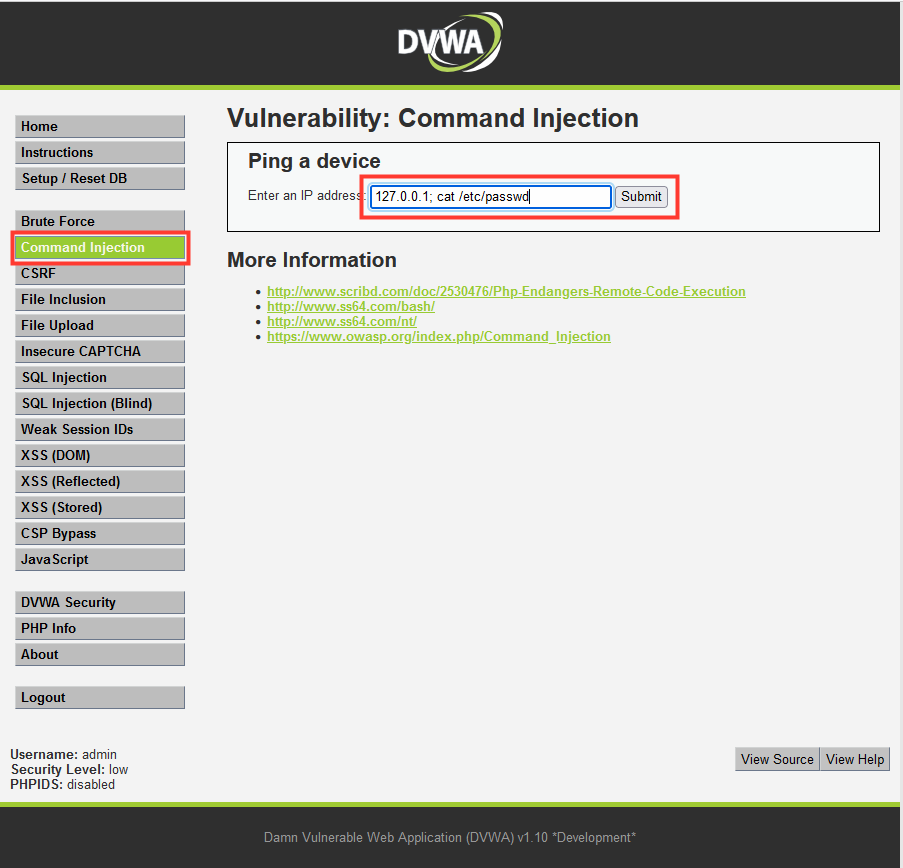
7. DVWA Command Injection
- Select: Command Injection
- User ID:
127.0.0.1; cat /etc/passwd
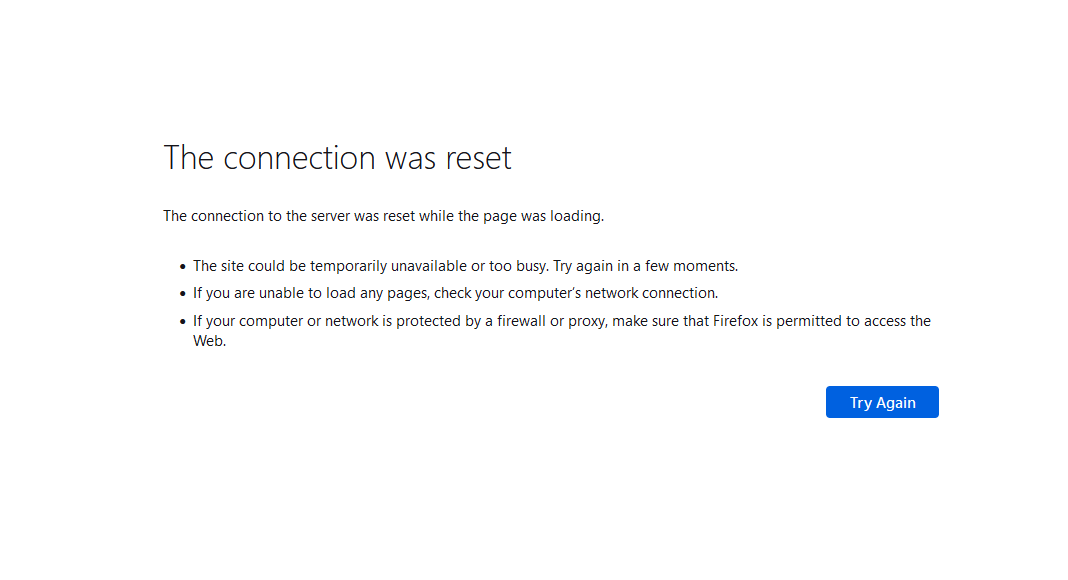
8.1 We configured the Command Injection filter to Block, so instead of the attack being permitted a timeout occurs.
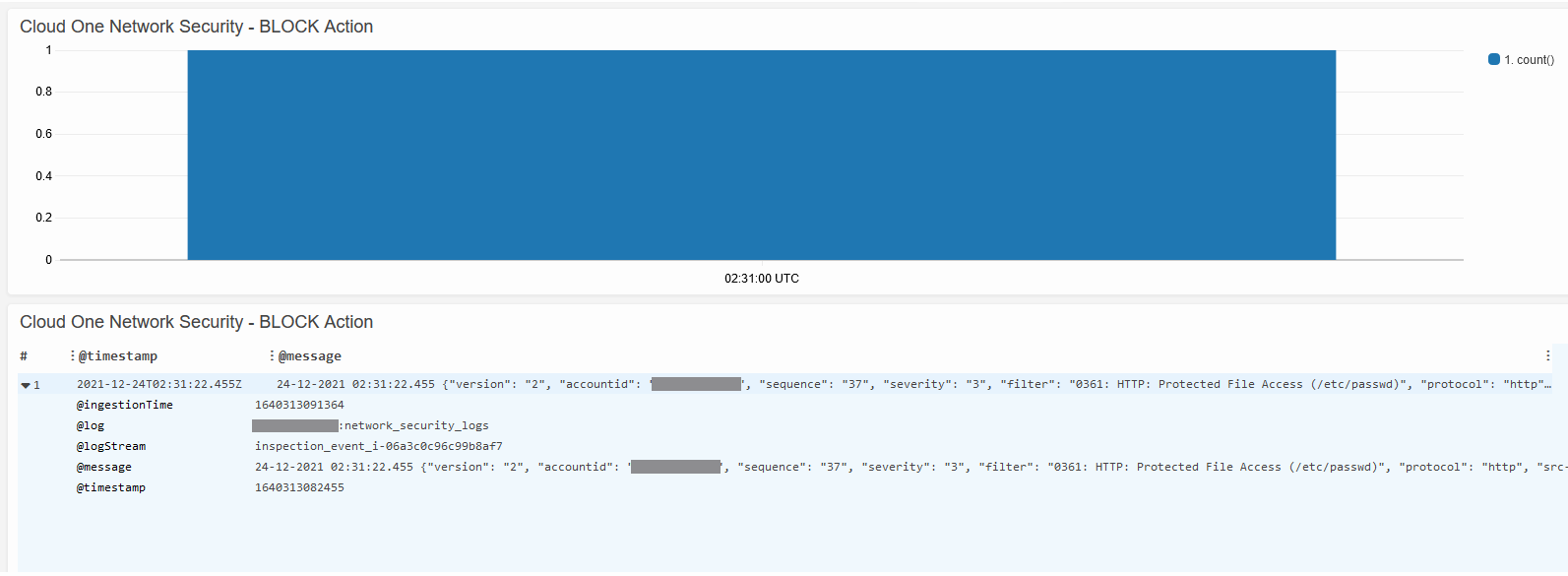
8.2 Let’s check our CloudWatch dashboard for the RCE event.
- In AWS Console navigate to CloudWatch
- From the left-hand menu select Dashboards
- Select: Cloud_One_Network_Security_Panel
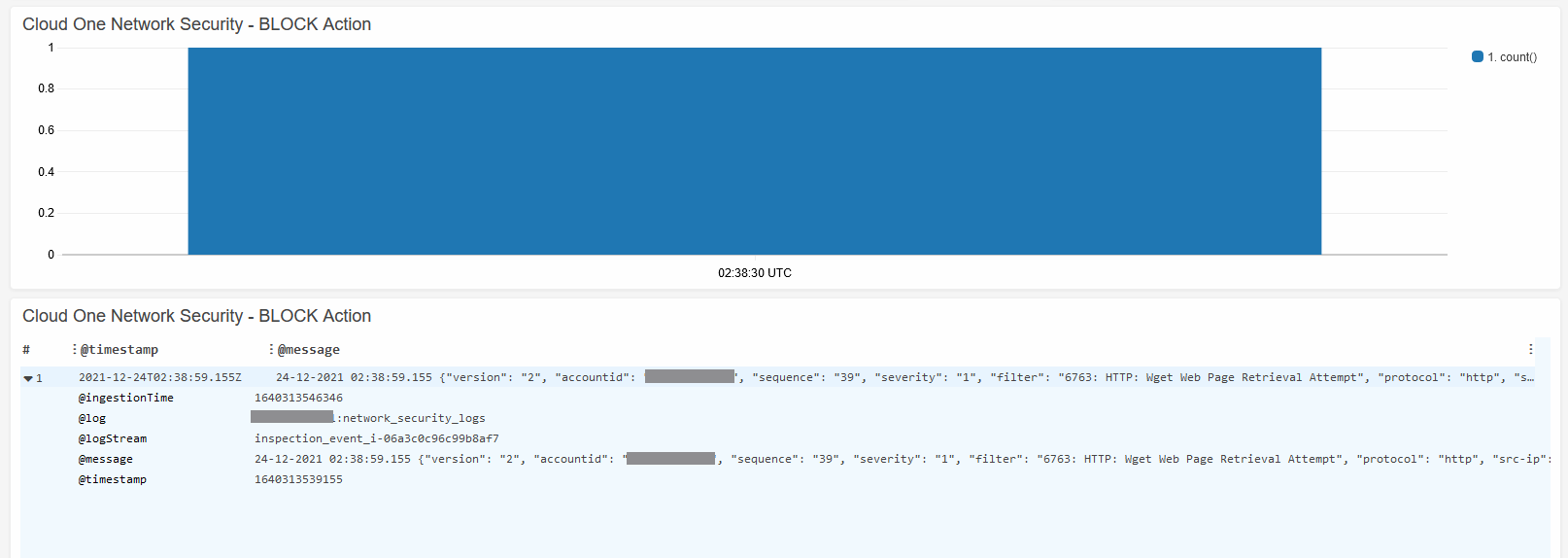
- Check under Cloud One Network Security - BLOCK Action
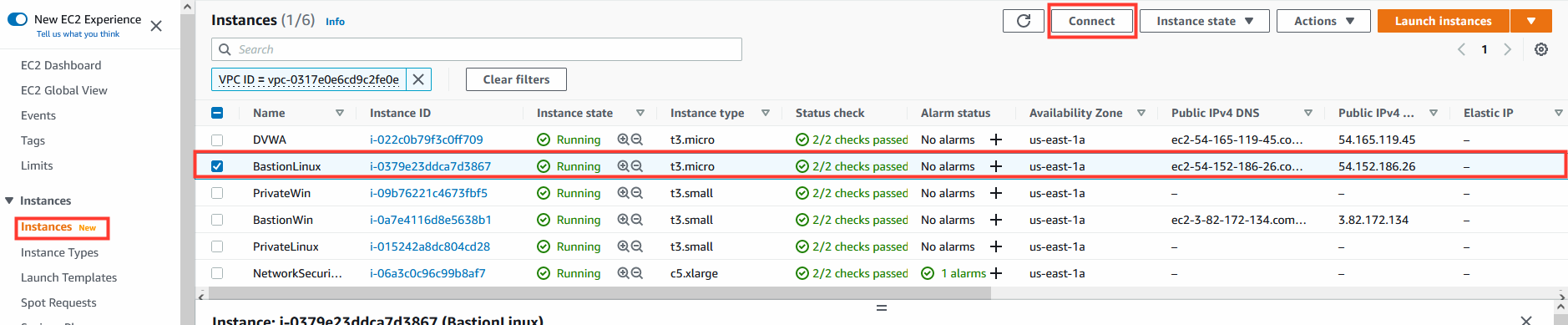
9. SSH to bastion machine
- In the AWS Console navigate to EC2
- Select EC2 instance: BastionLinux
- Click Connect
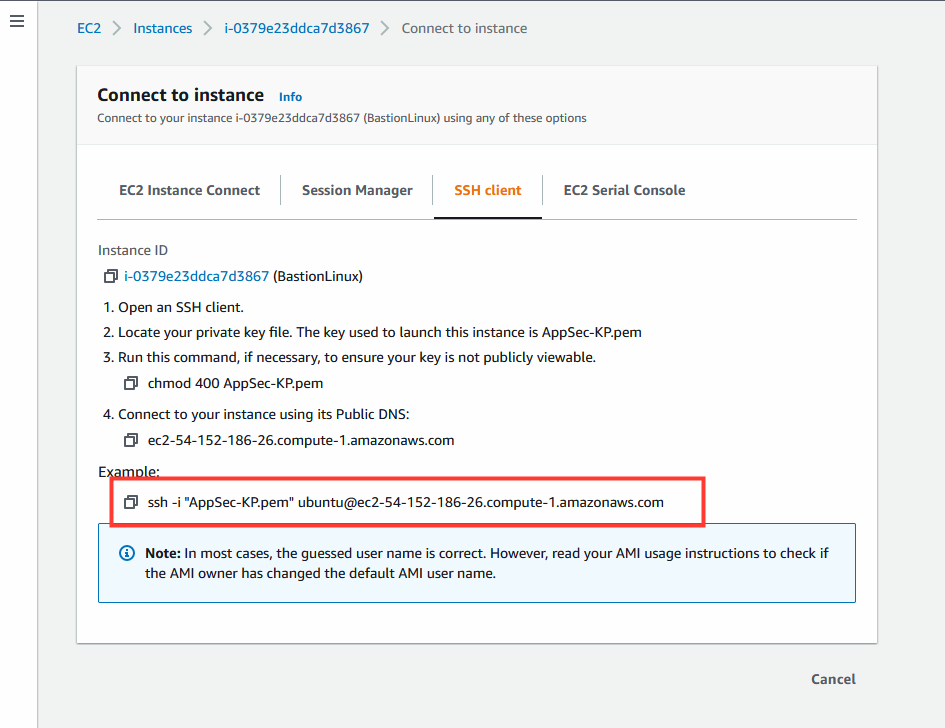
- Select tab: SSH client
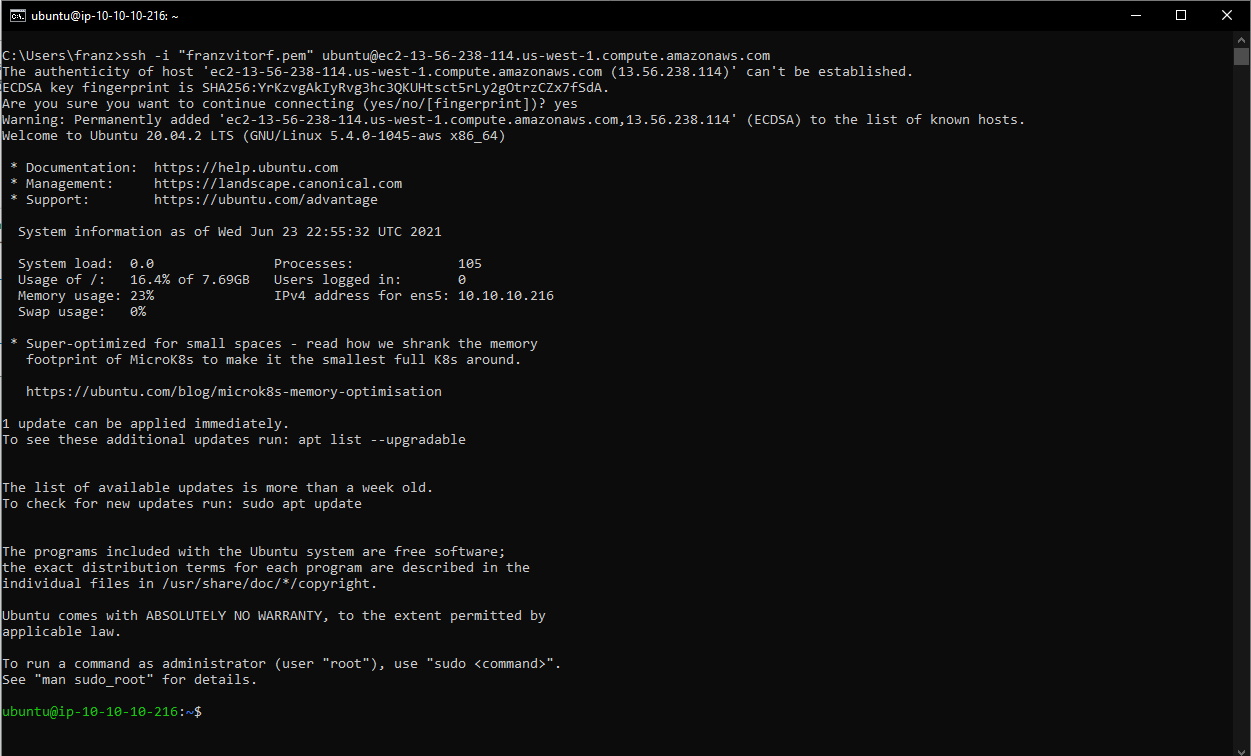
- Use the SSH Client to connect to the BastionLinux machine.
9.1 Wget Retrieval Attempt - Download Files
- In the SSH shell/terminal
- Run Command:
wget http://files.trendmicro.com/products/eicar-file/eicar.com
9.2 Remember we configured the intrusion prevention filter to Block, so instead of the file being permitted the Network Security Appliance drops the file attempt and another timeout will occur.
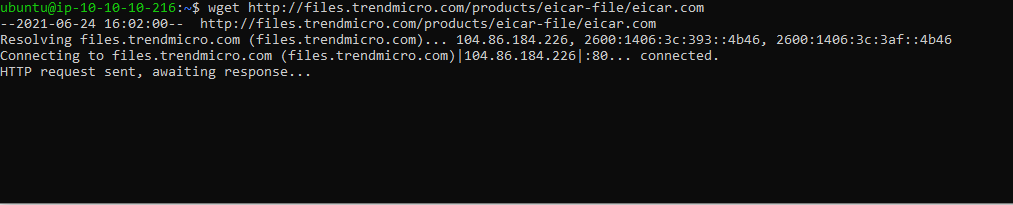
9.3 Let’s check our CloudWatch dashboard for Wget Retrieval Attempt - Download File
- In AWS Console navigate to CloudWatch
- From the left-hand menu select Dashboards
- Select: Cloud_One_Network_Security_Panel
- Check under Cloud One Network Security - BLOCK Action